Data Recovery Lost by Computer Virus Infection
When files mysteriously stop opening or start to disappear entirely, it can be easy to suspect that the problem is the result of a computer virus. While that may be the case, the truth is that viruses are just one type of malware that can infect your machine and affect the files on your computer. We’ll take a look at what kinds of malware are out there, as well as the potential for prevention and recovery in these different situations using tools like Data Rescue, Drive Genius, and Data Backup.
Types of Malware
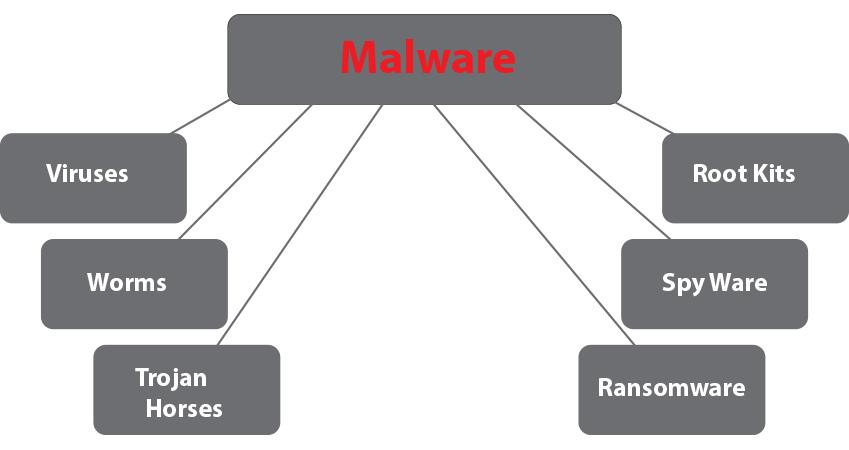
Malware is a portmanteau of the words malicious and software, meaning exactly what it sounds like: the term is used to refer to any application that is deliberately designed to damage or disrupt normal computer operations. This can include: damaging or corrupting files or the operating system, capturing private data, modifying or deleting data, and a range of other potentially negative actions.
Some types of malware, such as viruses and worms, are created with the purpose of infecting and attacking other computers after they have taken hold in a given system. Other malware (such as trojan horses, rootkits, and spyware) are designed to hide and avoid detection, and can often replicate themselves or modify the operating system to conceal their presence.
Here is some more information about these different malware categories and their effects:
Viruses are programs that attach themselves to other applications so that their malicious code is run when that application is launched. Many users refer to any infection or problem on their computer as a virus, but is actually a very specific type of attack, and just one category in the broader area of malware. The malicious actions taken by a virus after it is unknowingly run can vary greatly, but in many cases it can affect the integrity of your data or damage your operating system.
Worms are independent, standalone programs that replicate themselves and attempt to infect other computers, typically over a network. This can be a local or private network such as your home or workplace, or even public networks that collectively make up the internet. Worms can delete or affect your ability to access files in a variety of ways. For example, one of the first of these worms, The Morris Worm, was originally intended to measure the size of the internet. As it spread, the worm would infect individual computers multiple times, and each additional process would slow the computer down, eventually to the point that the system was unusable and no data on the machine could be accessed.
Trojan Horses are a type of malware that get their name from the story of the Greeks building a wooden horse to sneak into the city of Troy, posing the large statue as a gift of peace when it was actually filled with soldiers, allowing them to unlock the gates and gain the upper hand in the battle. In the same fashion, trojan horse malware applications are disguised as useful utilities in an attempt to trick users into running them, upon which their malicious code will then be launched. Trojan malware can take all sorts of harmful actions, many of which affect the files on your computer and can cause data loss.
Rootkits are a kind of malware designed to modify or replace programs to hide additional attacks. Rootkits most commonly modify or replace parts of your operating system, but they can exist in other levels of the computer from your boot instructions, your registry, all the way up to the normal applications you run on your computer. Normally, the best solution when dealing with a rootkit is to reinstall your operating system and restore data from backups or using a recovery tool, as rootkits can be extremely difficult to remove manually.
Spyware are independent malware applications that are designed to collect information about their host computer and the user of the computer. Some of these may scan files on your computer, monitor your keystrokes, snoop on your application usage, read your cookies, and more. While they may not directly affect the files on your computer, they can consume system resources and cause system instability and crashes, which could lead to a data recovery situation.
How to Stay Safe and Recover from Malware Attacks
The first line of defense when dealing with malicious software is to avoid attacks to begin with. This can be as simple as not clicking on emails or files from unknown senders, avoiding unfamiliar or suspicious looking websites and downloads, and connecting to known safe networks. Being proactive can only take you so far, and even the most cautious user is still at risk of being infected with malware. The next step is to install an anti-malware application, such as Drive Genius, that will automatically scan your computer and downloads for known malware using the latest definitions. Using such a utility will allow you to remove malware before it is opened or activated and its malicious code is run.
If you are in a situation where you were unable to prevent a malware attack from occurring and damage has already been done to your system or files, a data recovery software such as Data Rescue (available for both Mac and Windows) may still be able to help recover data. In many cases, Data Rescue is capable of recovering files that have been deleted by malware, or from a drive that fails to boot due to damage to the operating system caused by a virus or other type of malware. You will first want to make sure the malware has been removed from the system before recovery.
For deleted files, the application can be run like any other program, and if the computer fails to boot there are additional methods. On a Mac, you have the option of creating a bootable recovery USB drive on a working machine to use for recovery of a system that will no longer boot up, as well as the ability to connect to the problem computer using a firewire or thunderbolt cable and Target Disk Mode. On Windows, you can connect the problem drive to a working machine directly to scan it and recover files.
There are other malware situations in which recovery will not be possible. Ransomware attacks, most commonly in the form of trojan malware, have been on the rise in the past couple of years.
Ransomware is designed with a very specific purpose: to encrypt your files and demand payment for the decryption key. Unfortunately, if you find yourself in such a situation, there is no way for recovery software to restore the encrypted files. The best method of avoidance for ransomware is preventive, that means backing up important user and application data using a software utility like Data Backup for Mac and Windows. In the event of almost any malware attack, and especially ransomware, restoring from a backup is the simplest method of recovery.
About the Author
Ryan O.
My name is Ryan and I provide technical support and perform software testing for Prosoft Engineering, to ensure we provide customers with the best software experience possible. I also provide customer service for clients at The Data Rescue Center that have physically damaged devices. I enjoy helping customers maximize their chance of recovering and protecting their files, regardless of their potential data loss situation.